Ransomware has been holding our data hostage since 2013 when the infamous CryptoLocker first appeared. It is widely regarded as the most damaging and ubiquitous threat in the cyber security world, causing real life and immediate financial losses for individuals and businesses large and small. A recent report by Bitdefender suggests that 44% of ransomware victims in the UK have been left with no choice but to pay to recover their data. Read on to discover how we can stop these cyber thugs profiting from their devious extortion tactics.
What is Ransomware?
All ransomware variants have a common goal, to extort money from their victims through intimidation. The most frightening and also most common form of ransomware is CryptoWall, a family of file-encrypting malware that first appeared in early 2014. CryptoWall is notable for its unbreakable AES encryption and use of the Tor network (or dark web) for communicating with the infecting miscreant’s servers and bitcoin accounts.
In essence CryptoWall operates as follows:
- an infected email attachment or exploited web browser allows the “payload” to be delivered to a victim’s workstation
- the payload then irreversibly encrypts (password protects) all user data on local and network drives with an unbreakable pass key known only to the hostage takers
- it then quietly deletes all backups of encrypted files preventing restoration of your files
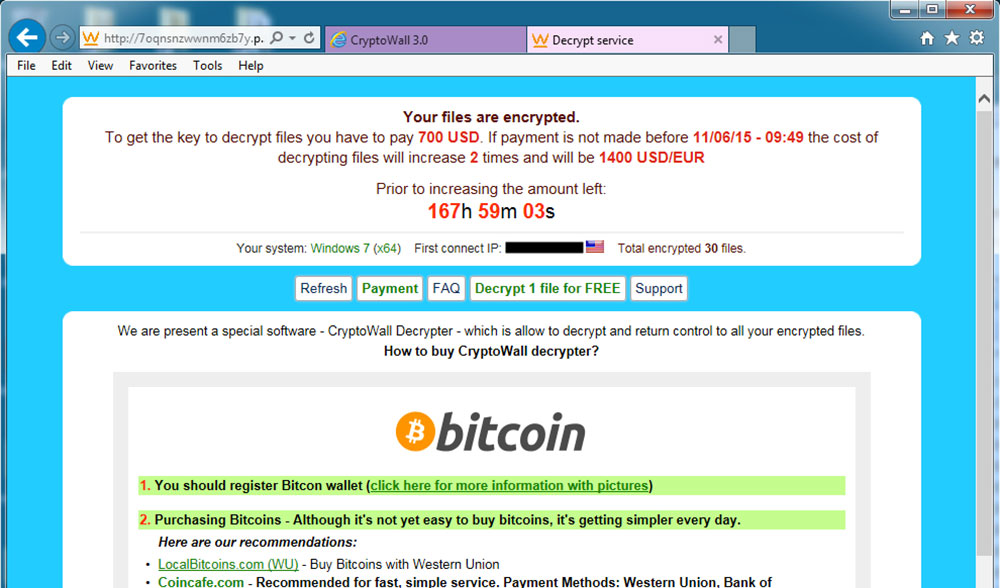
- finally, it displays a ransom note in Internet Explorer demanding payment for decryption of your files within a given time period
There is no way to access any of your files on your workstation or your company network shares until you have paid said ransom. Often the author of the CryptoWall attack will offer the victim a onetime free decryption service to prove that they do indeed have the required key to unlock the encrypted files.
Is this really going to happen to me?
CryptoWall has been noted as the “most successful piece of malware in history” according to this report. In 2016, ransomware is on the rise again. This is in part because it results in regular substantial returns for cyber attackers, but also because it’s incredibly easy to find ill prepared victims.
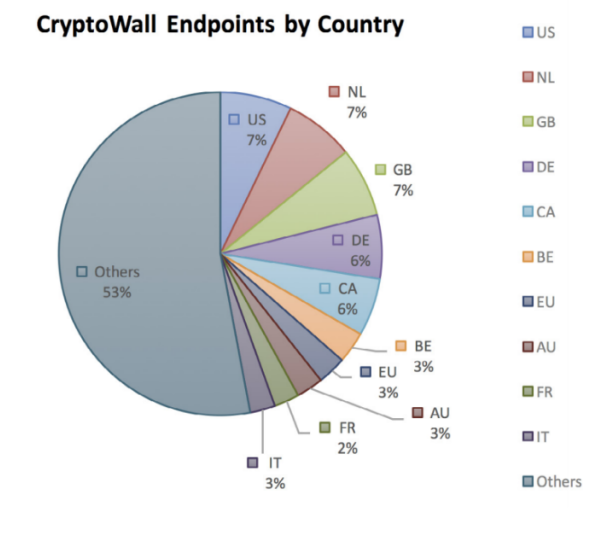
Don’t be lulled into the thinking that attackers won’t target the UK either. In fact the UK has the joint highest number of victims alongside the US and the Netherlands. Considering the small size of the UK compared to other countries, it would appear that we are being heavily targeted.
Most concerning of all though is that each time a variant is painstakingly beaten by the cyber security industry, a new iteration evolves to bypass those security measures. The latest iteration, CryptoWall 4.0, is still unbeatable according to the cyber security professional community.
Ultimately the only defence is to prepare for the worst.
How can I prevent or prepare for a Ransomware attack?
 Maintain and Protect Daily Backups
Maintain and Protect Daily Backups
Backups are obvious, but not everyone thinks to copy or move those backups to a secure, off network location. Ransomware will often encrypt your backup files too if it can access them on your internal network.
- Maintain daily backups
- Keep a copy of data offsite or in the Cloud
- Backup data AND server operating system states
 Use Email Wisely
Use Email Wisely
Email is as old as the Internet itself and no doubt it’s here to stay. Despite the meteoric rise of social media, we use it more and more every day, particularly in the workplace. For this reason it remains one of the most commonly exploited delivery methods for ransomware. Used correctly, email is safe, but be wary of the pitfalls.
- Use spam protection
- Check all email for suspicious content
- Never click links you weren’t expecting
- Never send personal information by email
 Use Trusted, Reliable, Updated Software
Use Trusted, Reliable, Updated Software
Your first line of defence when your device becomes infected. Never underestimate the importance of using the most up to date software.
- Maintain security software and scan regularly
- Keep browser up to date
- Use browser security extensions
- Update operating system regularly
 Browse Responsibly
Browse Responsibly
Much like human disease, the easiest way to avoid cyber infection is to avoid the infected.
- Avoid these kinds of sites:
- “free” software
- peer-to-peer file sharing
- out of date copyright
- non-profit organisations
- religious groups / places of worship
- personal web pages
- Block adverts with an ad-blocker
- Never download from unknown sources
- Never install software from pop ups
 Treat Public Networks as Unsafe
Treat Public Networks as Unsafe
Hackers can easily manipulate public networks to infect your device and obtain secure information. Public networks make much easier targets for the hacker since you are not protected from them behind your private network’s Internet firewall.
- Use operating system security measures – “Public Network”
- Use a secure VPN to connect to trusted network
- Password protected WiFi is still public
 Choose the Right IT Support Partner
Choose the Right IT Support Partner
Bristol Technology Group has you covered. We offer the following services to help keep you protected from cyber threats when online
- Enterprise grade secured VPNs
- Cyber security news @BristolTech
- Comprehensive IT support network
- Free security audits to all customers
- Private, secure Cloud backup services
- Contingency planning and disaster recovery